You can access the Volatility room here.
Task 10: Practical Investigations
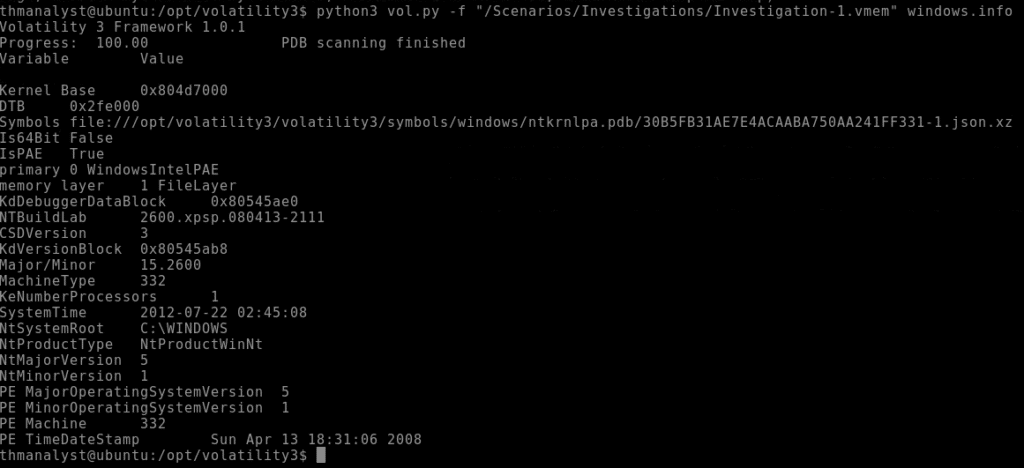
Question 1 – What is the build version of the host machine in Case 001?
Answer: 2600.xpsp.080413-2111
Question 2 – At what time was the memory file acquired in Case 001?
Answer: 2012-07-22 02:45:08
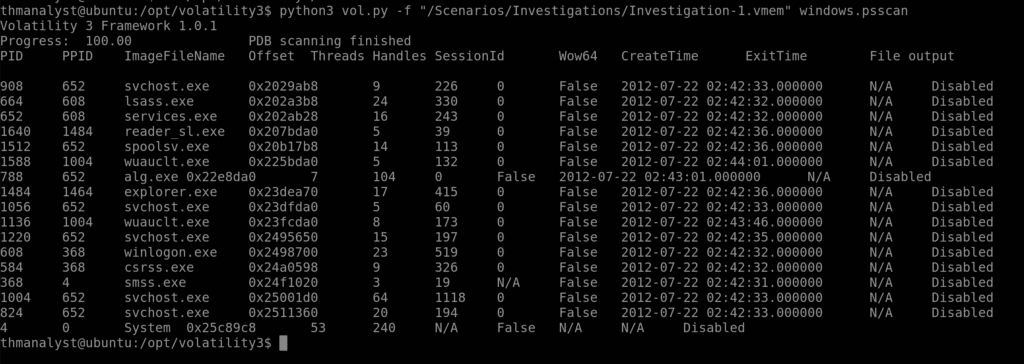
Question 3 –
What process can be considered suspicious in Case 001?
Note: Certain special characters may not be visible on the provided VM. When doing a copy-and-paste, it will still copy all characters.
Answer: reader_sl.exe
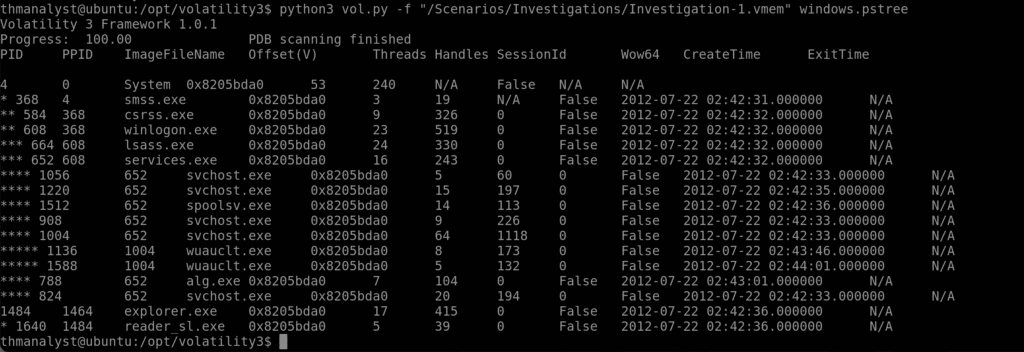
Question 4 – What is the parent process of the suspicious process in Case 001?
Answer: explorer.exe
Question 5 – What is the PID of the suspicious process in Case 001?
Answer: 1640
Question 6 – What is the parent process PID in Case 001?
Answer: 1484
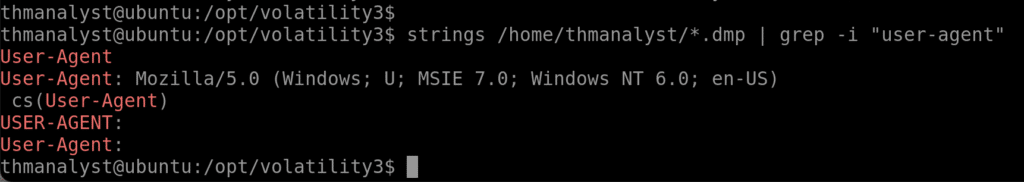
Question 7 – What user-agent was employed by the adversary in Case 001?
Answer: Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)
Question 8 – Was Chase Bank one of the suspicious bank domains found in Case 001? (Y/N)
Answer: Y
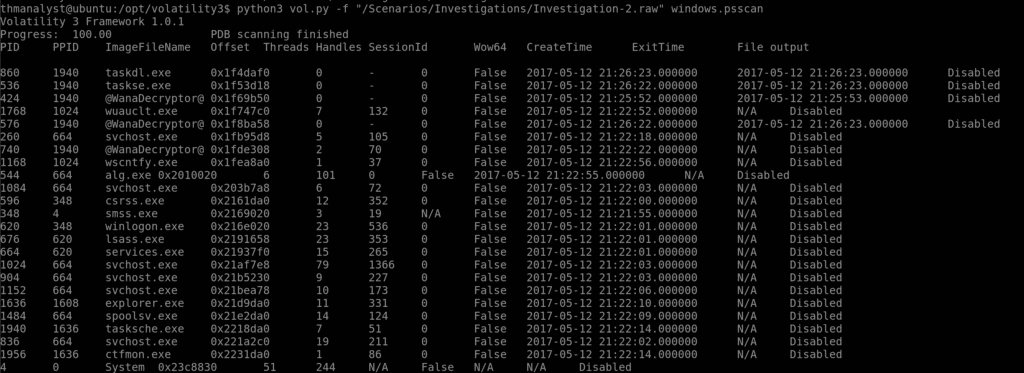
Question 9 – What suspicious process is running at PID 740 in Case 002?
Answer: @WannaDecryptor@
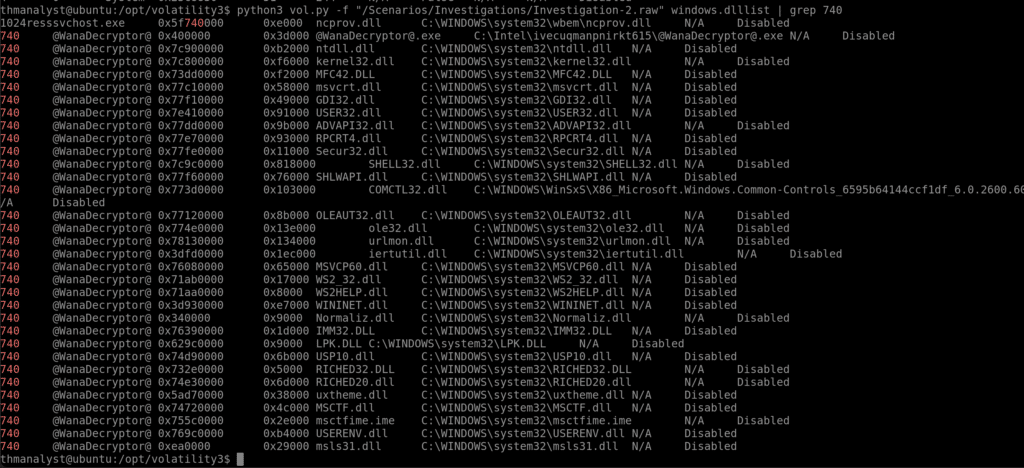
Question 10 – What is the full path of the suspicious binary in PID 740 in Case 002?
Answer: C:\Intel\ivecuqmanpnirkt615\@[email protected]
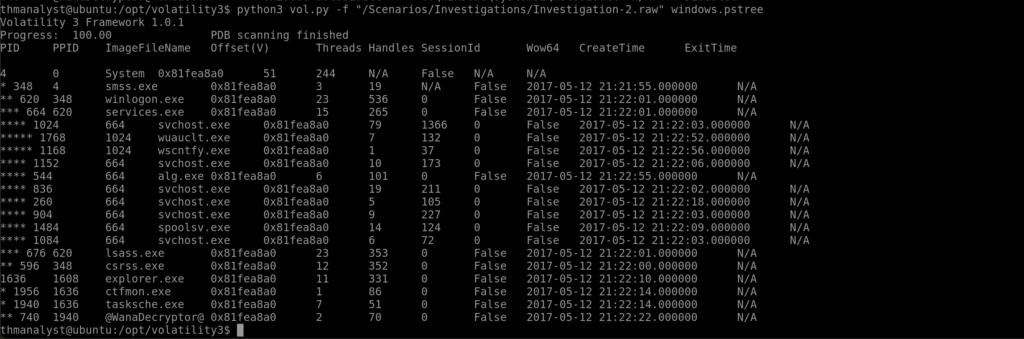
Question 11 – What is the parent process of PID 740 in Case 002?
Answer: tasksche.exe
Question 12 – What is the suspicious parent process PID connected to the decryptor in Case 002?
Answer: 1940
Question 13 – From our current information, what malware is present on the system in Case 002?
Answer: WannaCry
Question 14 – What DLL is loaded by the decryptor used for socket creation in Case 002?
Answer: ws2_32.dll
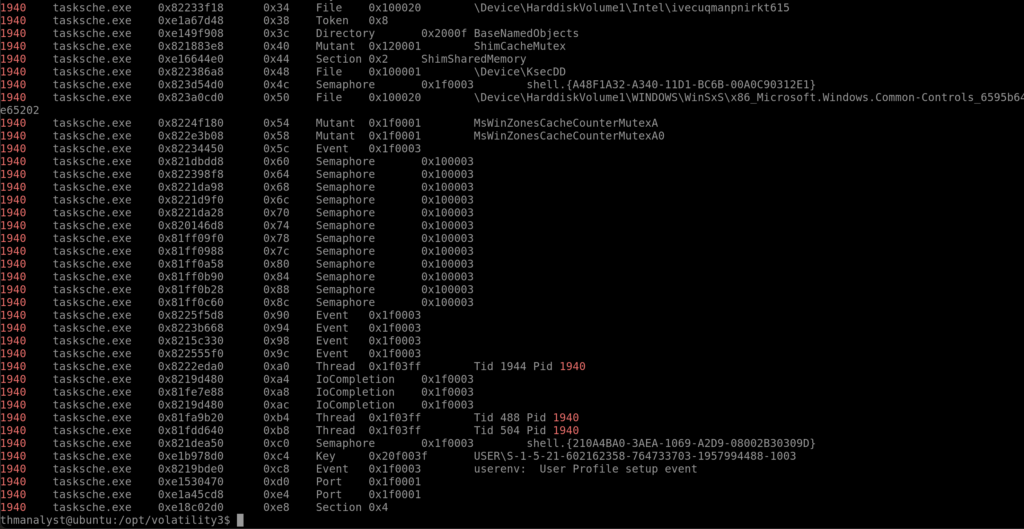
Question 15 – What mutex can be found that is a known indicator of the malware in question in Case 002?
Answer: **************************** (THE ANSWER IS IN ABOVE IMAGE)
Question 16 – What plugin could be used to identify all files loaded from the malware working directory in Case 002?
Answer: windows.[********] (FIND YOURSELF FOR THIS ONE LOL :P)